今回は、Linuxのセキュリティに問題のある設定、状態を指摘してくれるツール『LYNIS』を紹介する。 セキュリティに問題がある設定とは、パスワードの無いユーザが存在していたり、パーティションの設定で問題のあるファイルの有無などが該当する。
さて、早速インストールして使ってみよう。
1.インストール
以下のコマンドを実行し、インストールを行う。
sudo apt-get install lynis (Debian/Ubuntuの場合)
sudo yum install lynis (RHEL系の場合)2.コマンドの実行
さて、それでは実際にコマンドを実行してみよう。 注意したい点として、このコマンドはroot権限が必要となるため、rootユーザもしくはsudoをつけて実行を行う必要がある。 オプション無しで実行すると、ヘルプ情報が表示される。
[root@test-centos ~]# lynis
[ Lynis 1.5.9 ]
##############################################################################
Lynis comes with ABSOLUTELY NO WARRANTY. This is free software, and you are
welcome to redistribute it under the terms of the GNU General Public License.
See the LICENSE file for details about using this software.
Copyright 2007-2014 - Michael Boelen, http://cisofy.com
Enterprise support and plugins available via CISOfy - http://cisofy.com
##############################################################################
[+] Initializing program
------------------------------------
Scan options:
--auditor "<name>" : Auditor name
--check-all (-c) : Check system
--no-log : Don't create a log file
--profile <profile> : Scan the system with the given profile file
--quick (-Q) : Quick mode, don't wait for user input
--tests "<tests>" : Run only tests defined by <tests>
--tests-category "<category>" : Run only tests defined by <category>
Layout options:
--no-colors : Don't use colors in output
--quiet (-q) : No output, except warnings
--reverse-colors : Optimize color display for light backgrounds
Misc options:
--check-update : Check for updates
--debug : Debug logging to screen
--view-manpage (--man) : View man page
--version (-V) : Display version number and quit
Enterprise options:
--plugin-dir "<path"> : Define path of available plugins
--upload : Upload data to central node
Error: No parameters specified!
See man page and documentation for all available options.
Exiting..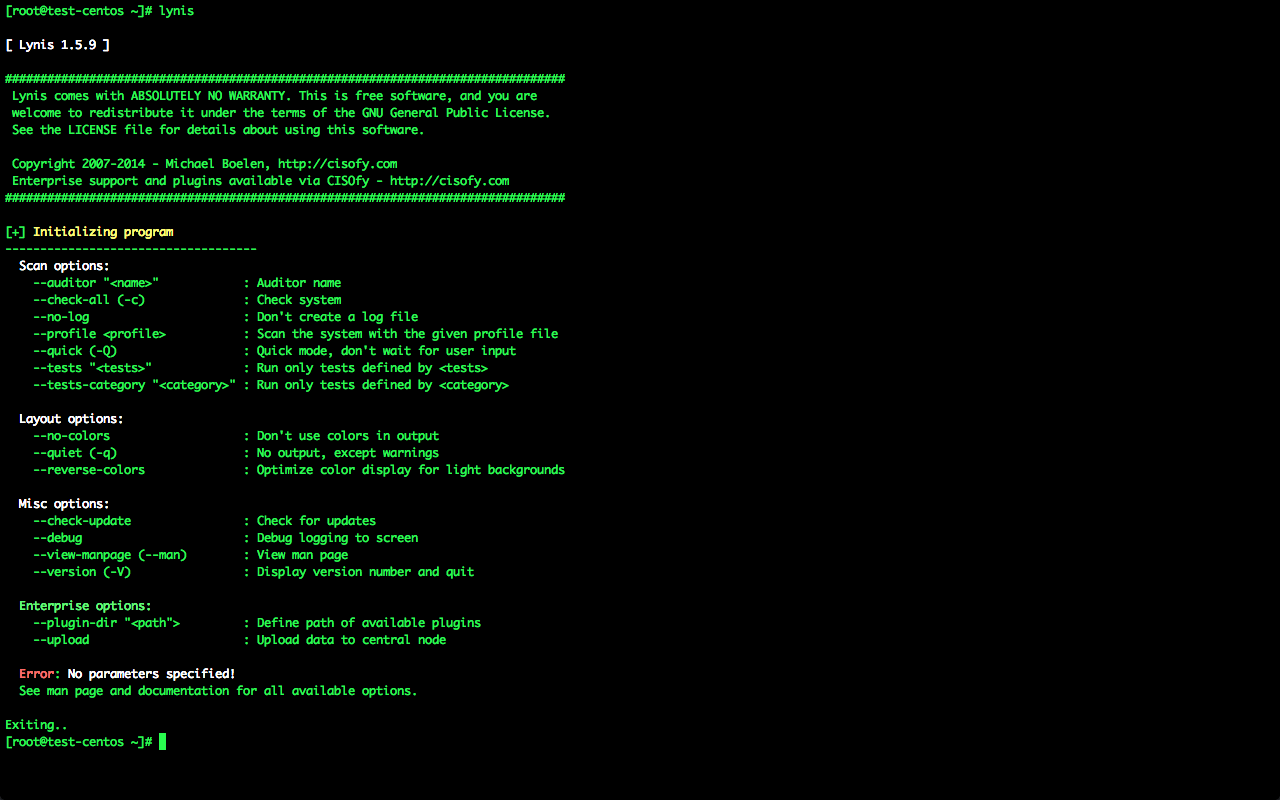
Scan optionsの箇所を見ると、フルチェックは「-c」オプションで実行できるようだ。
それでは、実際にやってみよう。
[root@test-centos ~]# lynis -c
[ Lynis 1.5.9 ]
##############################################################################
Lynis comes with ABSOLUTELY NO WARRANTY. This is free software, and you are
welcome to redistribute it under the terms of the GNU General Public License.
See the LICENSE file for details about using this software.
Copyright 2007-2014 - Michael Boelen, http://cisofy.com
Enterprise support and plugins available via CISOfy - http://cisofy.com
##############################################################################
[+] Initializing program
------------------------------------
- Detecting OS... [ DONE ]
- Clearing log file (/var/log/lynis.log)... [ DONE ]
---------------------------------------------------
Program version: 1.5.9
Operating system: Linux
Operating system name: CentOS
Operating system version: CentOS release 6.5 (Final)
Kernel version: 2.6.32-431.11.2.el6.x86_64
Hardware platform: x86_64
Hostname: test-centos
Auditor: [Unknown]
Profile: /etc/lynis/default.prf
Log file: /var/log/lynis.log
Report file: /var/log/lynis-report.dat
Report version: 1.0
Plugin directory: /usr/share/lynis/plugins
---------------------------------------------------
[ Press [ENTER] to continue, or [CTRL]+C to stop ]
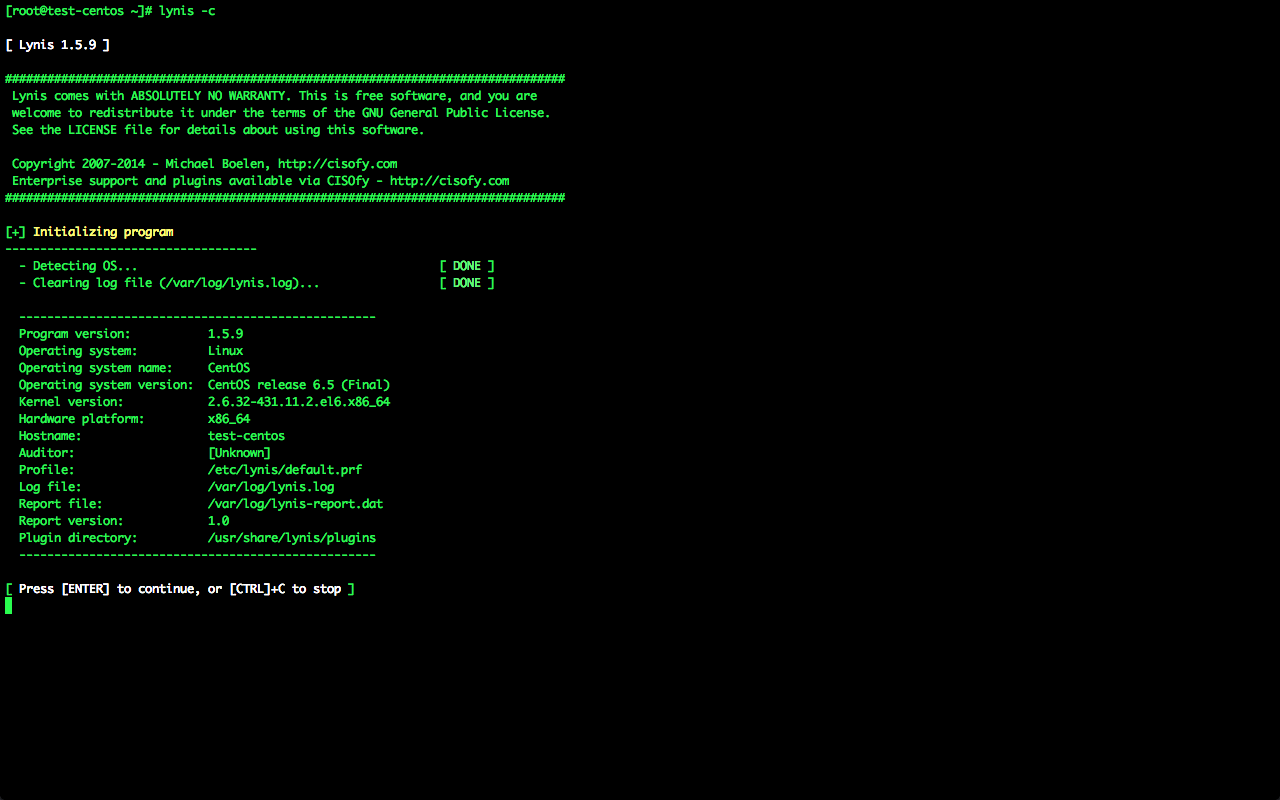
まずはOSの基本的な情報が表示される。 それ以降の情報を表示させるにはEnterキー、途中でキャンセルするならばCtrl + Cキーを押下する。
以下、それ以降の情報のサンプル
[+] System Tools
------------------------------------
- Scanning available tools...
- Checking system binaries...
- Checking /bin... [ FOUND ]
- Checking /sbin... [ FOUND ]
- Checking /usr/bin... [ FOUND ]
- Checking /usr/sbin... [ FOUND ]
- Checking /usr/local/bin... [ FOUND ]
- Checking /usr/local/sbin... [ FOUND ]
- Checking /usr/local/libexec... [ FOUND ]
- Checking /usr/libexec... [ FOUND ]
- Checking /usr/sfw/bin... [ NOT FOUND ]
- Checking /usr/sfw/sbin... [ NOT FOUND ]
- Checking /usr/sfw/libexec... [ NOT FOUND ]
- Checking /opt/sfw/bin... [ NOT FOUND ]
- Checking /opt/sfw/sbin... [ NOT FOUND ]
- Checking /opt/sfw/libexec... [ NOT FOUND ]
- Checking /usr/xpg4/bin... [ NOT FOUND ]
- Checking /usr/css/bin... [ NOT FOUND ]
- Checking /usr/ucb... [ NOT FOUND ]
- Checking /usr/X11R6/bin... [ NOT FOUND ]
- Checking /usr/X11R7/bin... [ NOT FOUND ]
[ Press [ENTER] to continue, or [CTRL]+C to stop ]
(省略)
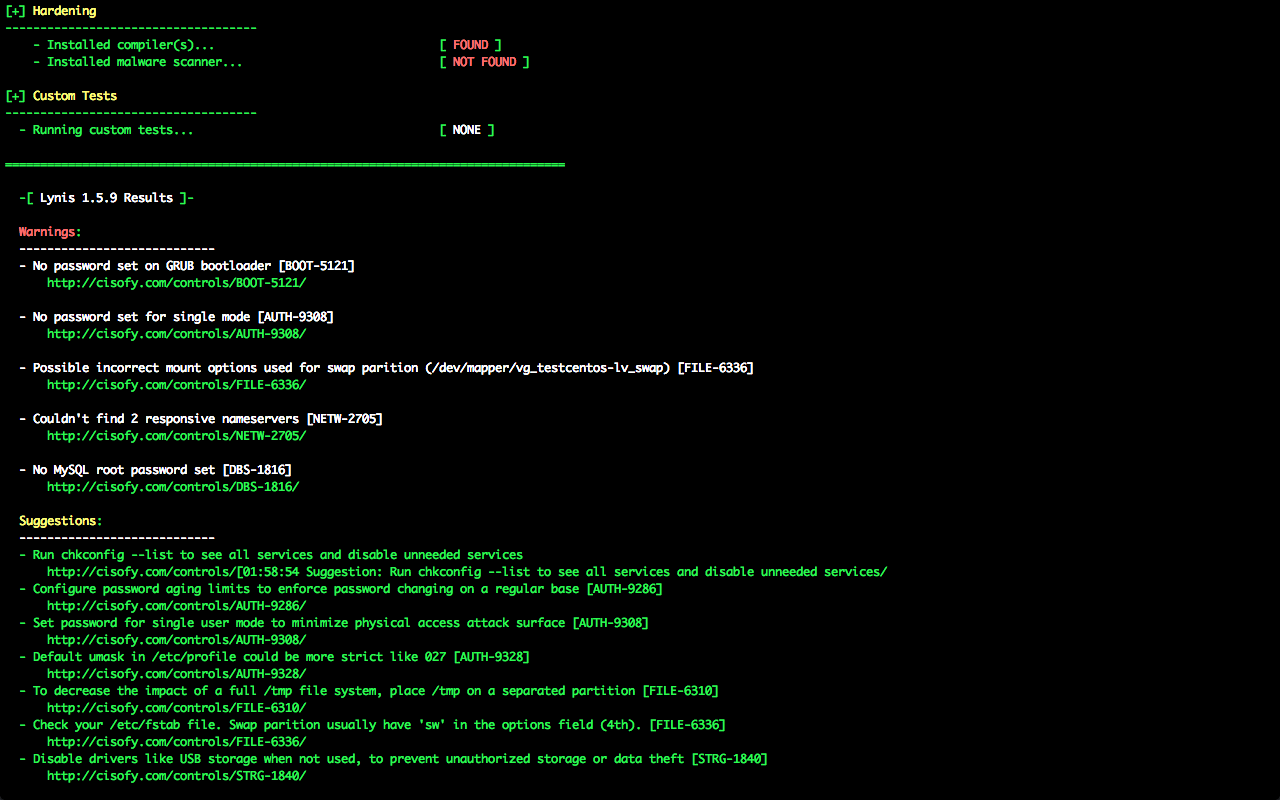
最終的に、以下のように対応策を表示してくれる。
================================================================================
-[ Lynis 1.5.9 Results ]-
Warnings:
----------------------------
- No password set on GRUB bootloader [BOOT-5121]
http://cisofy.com/controls/BOOT-5121/
- No password set for single mode [AUTH-9308]
http://cisofy.com/controls/AUTH-9308/
- Possible incorrect mount options used for swap parition (/dev/mapper/vg_testcentos-lv_swap) [FILE-6336]
http://cisofy.com/controls/FILE-6336/
- Couldn't find 2 responsive nameservers [NETW-2705]
http://cisofy.com/controls/NETW-2705/
- No MySQL root password set [DBS-1816]
http://cisofy.com/controls/DBS-1816/
Suggestions:
----------------------------
- Run chkconfig --list to see all services and disable unneeded services
http://cisofy.com/controls/[01:58:54 Suggestion: Run chkconfig --list to see all services and disable unneeded services/
- Configure password aging limits to enforce password changing on a regular base [AUTH-9286]
http://cisofy.com/controls/AUTH-9286/
- Set password for single user mode to minimize physical access attack surface [AUTH-9308]
http://cisofy.com/controls/AUTH-9308/
- Default umask in /etc/profile could be more strict like 027 [AUTH-9328]
http://cisofy.com/controls/AUTH-9328/
- To decrease the impact of a full /tmp file system, place /tmp on a separated partition [FILE-6310]
http://cisofy.com/controls/FILE-6310/
- Check your /etc/fstab file. Swap parition usually have 'sw' in the options field (4th). [FILE-6336]
http://cisofy.com/controls/FILE-6336/
- Disable drivers like USB storage when not used, to prevent unauthorized storage or data theft [STRG-1840]
http://cisofy.com/controls/STRG-1840/
- Disable drivers like firewire storage when not used, to prevent unauthorized storage or data theft [STRG-1846]
http://cisofy.com/controls/STRG-1846/
- Check DNS configuration for the dns domain name [NAME-4028]
http://cisofy.com/controls/NAME-4028/
- Add the IP name and FQDN to /etc/hosts for proper name resolving [NAME-4404]
http://cisofy.com/controls/NAME-4404/
- Check your resolv.conf file and fill in a backup nameserver if possible [NETW-2705]
http://cisofy.com/controls/NETW-2705/
- Access to CUPS configuration could be more strict. [PRNT-2307]
http://cisofy.com/controls/PRNT-2307/
- Configure a firewall/packet filter to filter incoming and outgoing traffic [FIRE-4590]
http://cisofy.com/controls/FIRE-4590/
- Install Apache mod_evasive to guard webserver against DoS/brute force attempts [HTTP-6640]
http://cisofy.com/controls/HTTP-6640/
- Install Apache mod_qos to guard webserver against Slowloris attacks [HTTP-6641]
http://cisofy.com/controls/HTTP-6641/
- Install Apache mod_spamhaus to guard webserver against spammers [HTTP-6642]
http://cisofy.com/controls/HTTP-6642/
- Install Apache modsecurity to guard webserver against web application attacks [HTTP-6643]
http://cisofy.com/controls/HTTP-6643/
- Use mysqladmin to set a MySQL root password (mysqladmin -u root -p password MYPASSWORD) [DBS-1816]
http://cisofy.com/controls/DBS-1816/
- Check what deleted files are still in use and why. [LOGG-2190]
http://cisofy.com/controls/LOGG-2190/
- Add legal banner to /etc/motd, to warn unauthorized users [BANN-7122]
http://cisofy.com/controls/BANN-7122/
- Add a legal banner to /etc/issue, to warn unauthorized users [BANN-7126]
http://cisofy.com/controls/BANN-7126/
- Add legal banner to /etc/issue.net, to warn unauthorized users [BANN-7130]
http://cisofy.com/controls/BANN-7130/
- Audit daemon is enabled with an empty ruleset. Disable the daemon or define rules [ACCT-9630]
http://cisofy.com/controls/ACCT-9630/
- Check ntpq peers output for unreliable ntp peers and correct/replace them [TIME-3120]
http://cisofy.com/controls/TIME-3120/
- Some time servers missing in step-tickers file [TIME-3160]
http://cisofy.com/controls/TIME-3160/
- Install a file integrity tool [FINT-4350]
http://cisofy.com/controls/FINT-4350/
- One or more sysctl values differ from the scan profile and could be tweaked [KRNL-6000]
http://cisofy.com/controls/KRNL-6000/
- Harden the system by removing unneeded compilers. This can decrease the chance of customized trojans, backdoors and rootkits to be compiled and installed [HRDN-7220]
http://cisofy.com/controls/HRDN-7220/
- Harden compilers and restrict access to world [HRDN-7222]
http://cisofy.com/controls/HRDN-7222/
- Harden the system by installing one or malware scanners to perform periodic file system scans [HRDN-7230]
http://cisofy.com/controls/HRDN-7230/
Follow-up:
----------------------------
- Check the logfile (less /var/log/lynis.log)
- Read security controls texts (http://cisofy.com)
- Use --upload to upload data (Lynis Enterprise users)
================================================================================
なお、「-Q」オプションを付与することでユーザ入力を省略できるようだ。 実行結果のログは「/var/log/lynis-report.dat」に格納されている。
うーん、結構便利な感じ?
なお、より細かく知りたい場合はこちらのブログを参考にすると良いだろう。

